- Tutorials Howto Workaround DevOps Code
- Credential or ssl vpn configuration is wrong
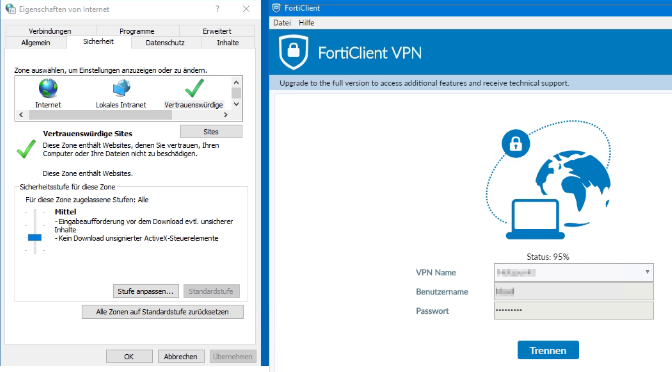
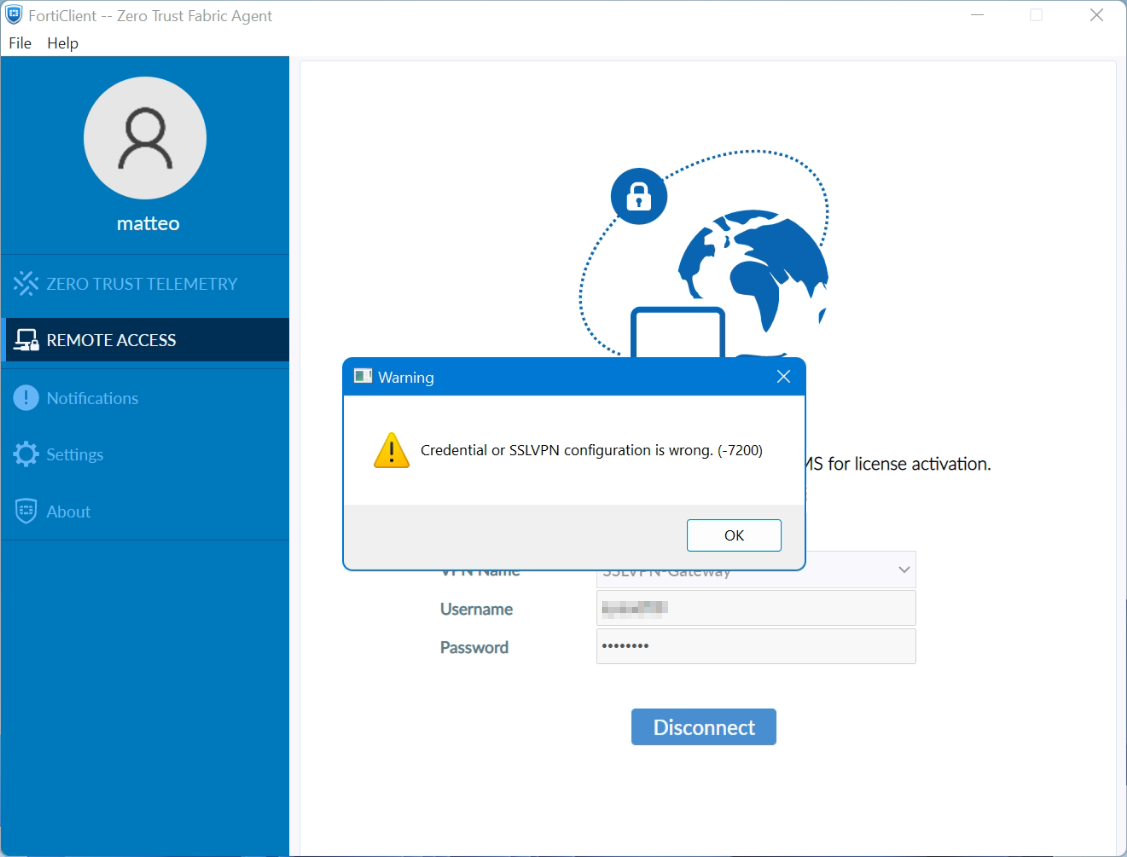
- FortiClient Error: Credential or ssl vpn configuration is wrong (-7200)
- How to solve ssl vpn failure
- Add website to Trusted sites
- Don’t get success yet ?
- Fortinet Community
- Technical Tip: Credential or SSL-VPN configuration is wrong (-7200) Radius user
- Fortinet Community
- Fortinet Community
- Fortinet Community
Tutorials Howto Workaround DevOps Code
Credential or ssl vpn configuration is wrong
FortiClient Error: Credential or ssl vpn configuration is wrong (-7200)
When trying to start an SSL VPN connection on a Windows 10, Windows Server 2016 or 2019 with the FortiClient, it may be that the error message “Credential or ssl vpn configuration is wrong (-7200)” appears. The reason to drop connection to the endpoint during initializing caused by the encryption, which can be found in the settings of the Internet options.
Another symptom can be determined, the SSL-VPN connection and authentication are successfully established, but remote devices cannot be reached, and ICMP replies are also missing and result in a timeout.
How to solve ssl vpn failure
According to Fortinet support, the settings are taken from the Internet options. The Internet Options of the Control Panel can be opened via Internet Explorer (IE), or by calling inetcpl.cpl directly.
Press the Win + R keys enter inetcpl.cpl and click OK.
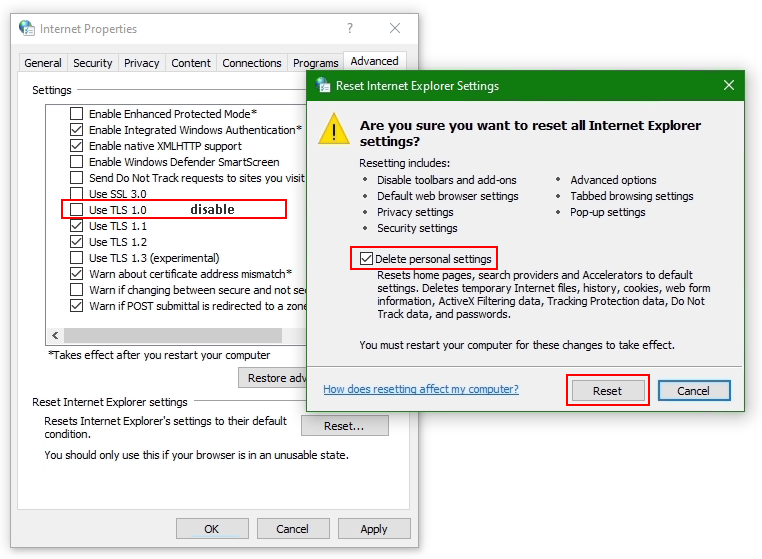
Select the Advanced tab
Click the Reset… button. If the Reset Internet Explorer settings button does not appear, go to the next step.
Click the Delete personal settings option
Click Reset
Open Internet Options again.
Go back to Advanced tab
Disable use TLS 1.0 (no longer supported)
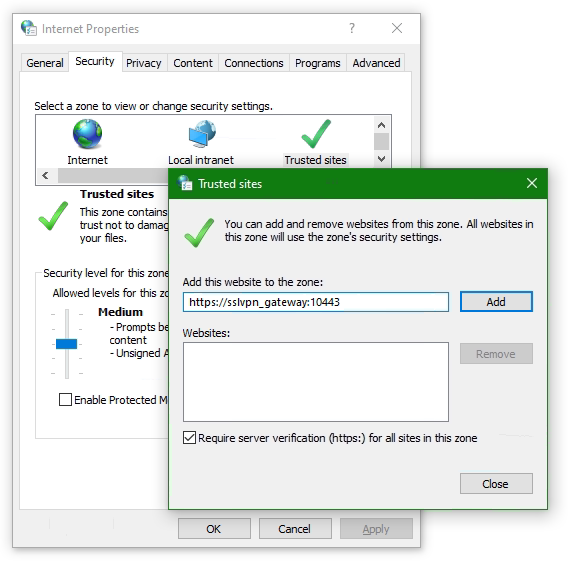
Add website to Trusted sites
Add the SSL-VPN gateway URL to the Trusted sites. Usually, the SSL VPN gateway is the FortiGate on the endpoint side.
Go to the Security tab in Internet Options and choose Trusted sites then click the button Sites. Insert the SSL-VPN gateway URL into Add this website to the zone and click Add, here like https://sslvpn_gateway:10443 as placeholder.
Note: The default Fortinet certificate for SSL VPN was used here, but using a validated certificate won’t make a difference.
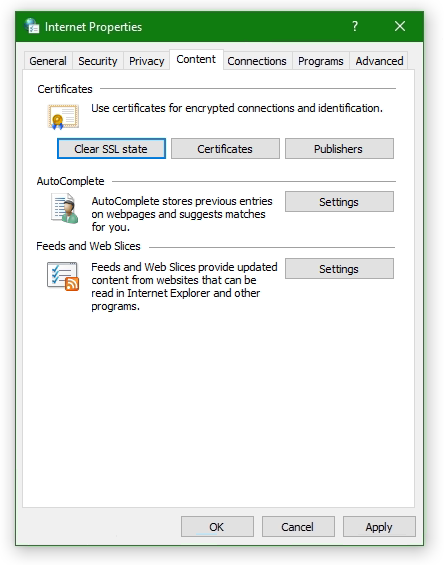
Furthermore, the SSL state must be reset, go to tab Content under Certificates. Click the Clear SSL state button.
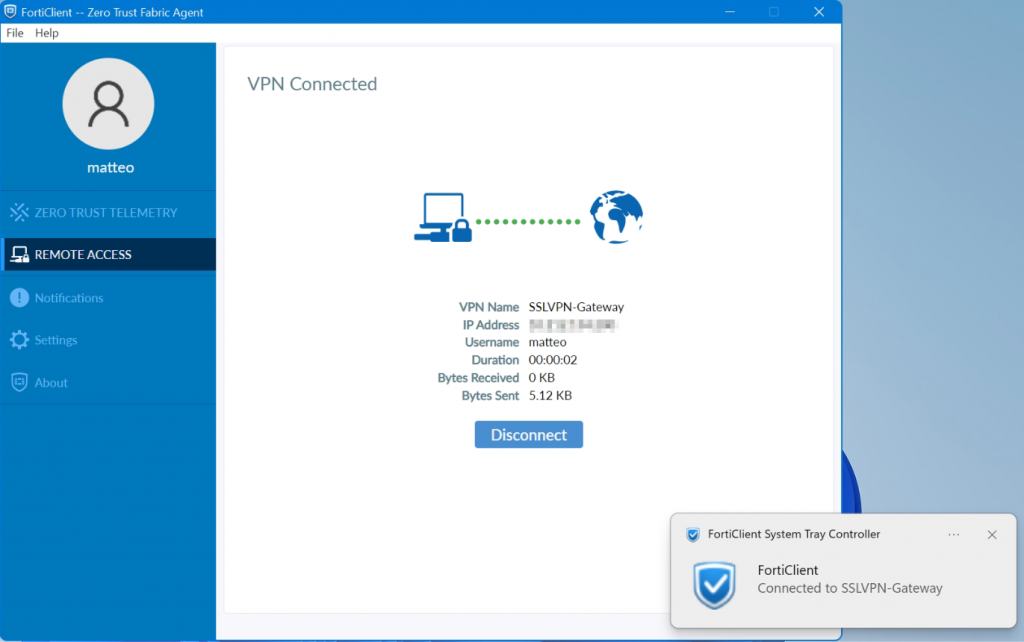
The SSL VPN connection should now be possible with the FortiClient version 6 or later, on Windows Server 2016 or later, also on Windows 10.
Don’t get success yet ?
If you haven’t had any success up to this point, don’t despair now, there is more help available, may the following is the case!
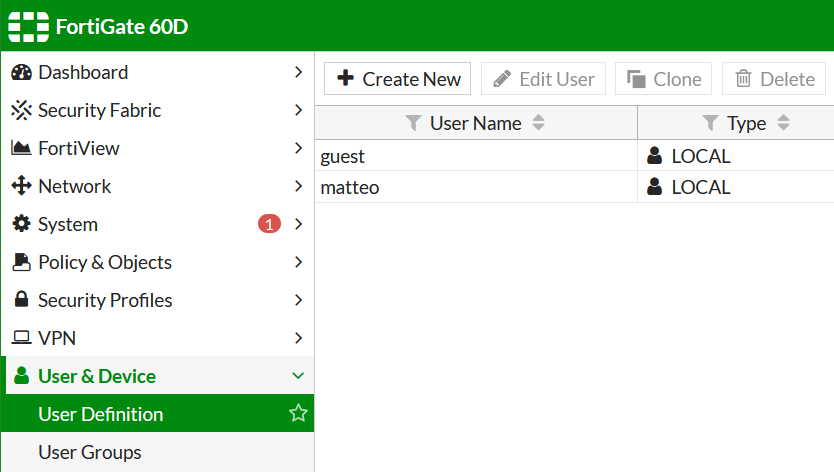
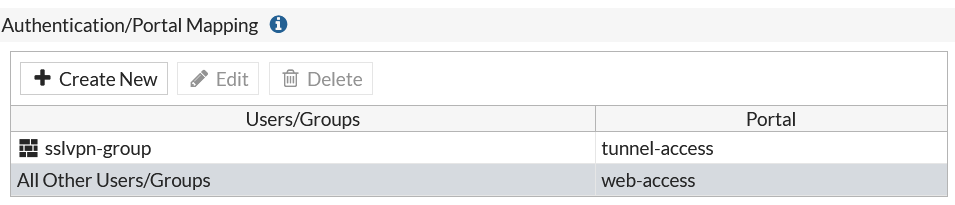
If you may use an FortiClient 7 on Windows 10 or Windows 11, then create a new local user on the FortiGate and add it to the SSL-VPN group.
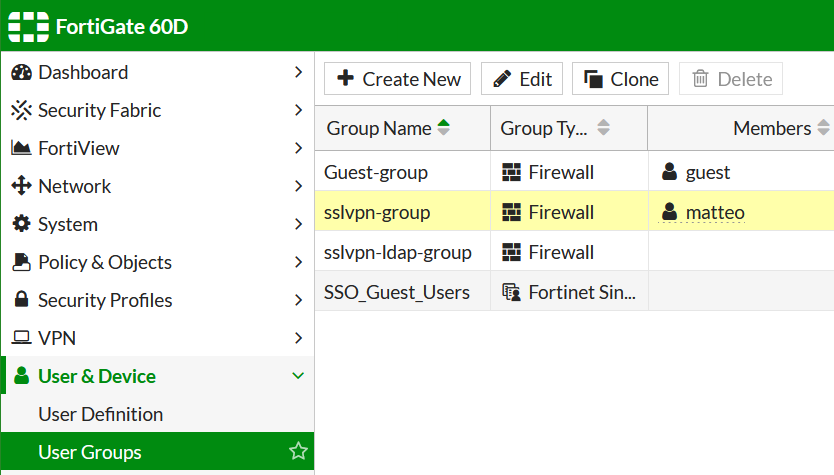
Add the user to the SSLVPN group assigned in the SSL VPN settings.
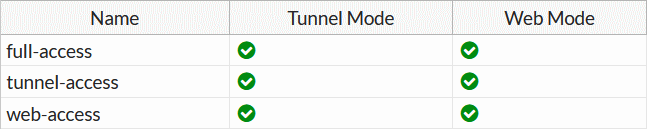
Try to verify the credentails using the web mode, for this in SSL-VPN Portals the Web Mode must my enabled.
Note that the group with the affected user is assigned under SSL-VPN Settings at Authentication/Portal Mapping.
Try to authenticate the vpn connection with this user.
It worked here with this attempt, but I haven’t yet been able to successfully carry out the authentication via LDAP server,
If your attempt was more successful and you know more ? please let us know and post your comment!
How useful was this post?
Click on a star to rate it!
Average rating 4.1 / 5. Vote count: 24
No votes so far! Be the first to rate this post.
We are sorry that this post was not useful for you!
Fortinet Community
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Created on 12-31-2021 01:08 AM Edited on 06-06-2022 11:44 AM By Anonymous
Technical Tip: Credential or SSL-VPN configuration is wrong (-7200) Radius user
| Description | This article describes how to troubleshoot the RADIUS issue for SSL-VPN. |
| Scope | FortiGate |
| Solution |